Today’s technology can permeate every aspect of your life. Protecting your personal and business interests from digital threats has become imperative. The interconnected nature of the digital landscape may present unprecedented opportunities, but it also exposes you to a myriad of cyber threats.
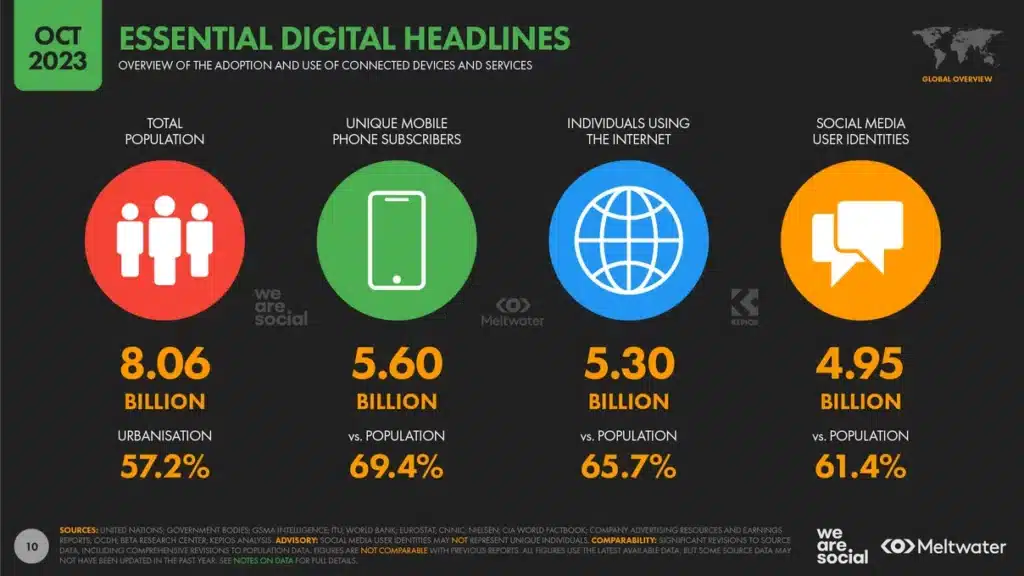
Source: DataReportal
Cybersecurity is your critical line of defense against malicious actors who wish to exploit vulnerabilities within your computer systems for financial gain, espionage, or disruption. This article explores the multifaceted realm of cybersecurity. We will discuss the challenges businesses and individuals face and offer insights into practical strategies for your protection.
Understanding the Cyber Threat Landscape
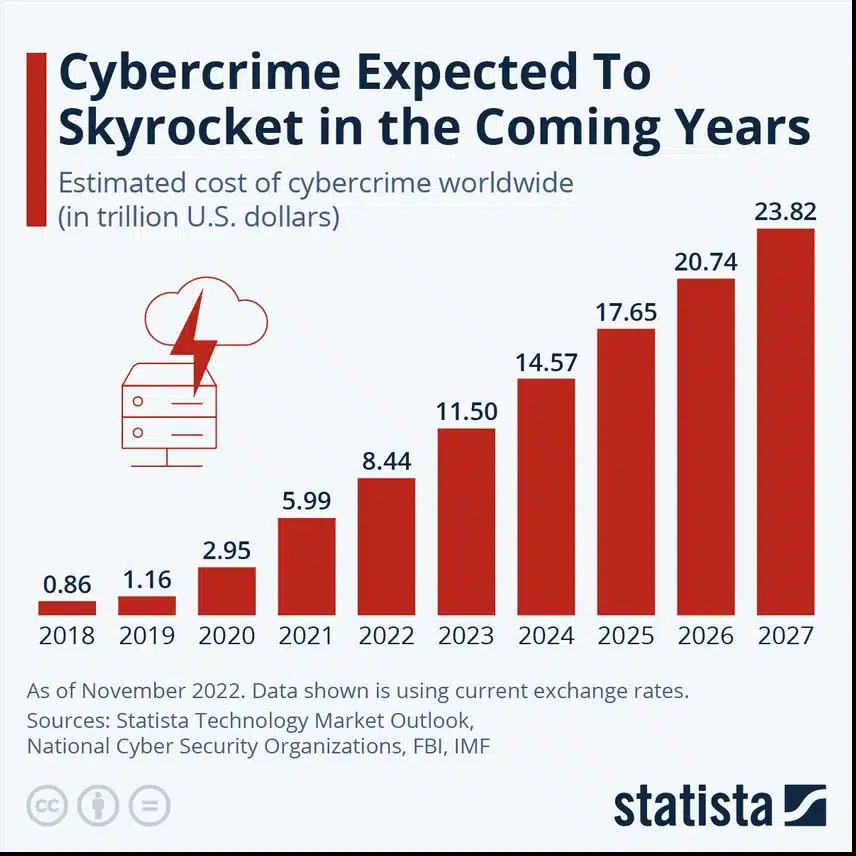
Source: Statista
The digital age has introduced a new age of connectivity and efficiency but has also given rise to complex and adapting cyber threats. Cyber threats can come in various forms. These include malware, phishing attacks, and advanced persistent threats (APTs).
These threats target large enterprises and individuals, making cybersecurity a concern for everyone.
Malware
Malicious software (malware) is a broad term encompassing various harmful software programs cybercriminals create. These programs aim to compromise your digital information’s confidentiality, integrity, or availability.
These nefarious programs allow them to break into systems, steal sensitive information, or disrupt daily operations. Often disguised as legitimate software, malware poses a significant risk to you and your organization.
- Viruses – A virus refers to a program that can attach itself to legitimate software and replicate when you execute it. Viruses spread across files, programs, and connected networks.
- Worms – Worms refer to self-replicating malware that does not require a host program to propagate. They spread independently across networks, exploiting vulnerabilities within your computer systems and consuming your system resources.
- Trojans (Trojan Horses) – Named after the ancient Greek story, Trojans disguise themselves as legitimate or benign software but contain hidden malicious functionalities. Once installed, they may create a backdoor to your computer system for remote access, stealing data, or performing other malicious activities.
- Ransomware – This type of malware encrypts your files or entire system, rendering them inaccessible. The cybercriminal utilizing the ransomware will then demand a ransom, usually in cryptocurrency, for the decryption key. Paying this ransom does not guarantee the recovery of your files.
- Spyware – Spyware monitors your activities without you knowing it. This malware can capture keystrokes, closely monitor web browsing habits, and meticulously collect sensitive information, such as login credentials and personal data.
- Adware – Adware displays unwanted advertisements on your device. In some cases, cybercriminals bundled it up with other malware.
- Rootkits – Rootkits are malware that allows unauthorized users to maintain access to your system while hiding their presence. They often replace or modify system files and are challenging to detect and remove.
- Fileless Malware – This type of malware operates in your system’s memory without leaving a footprint on the file system. For this reason, fileless malware can be challenging to detect using traditional antivirus solutions.
Phishing
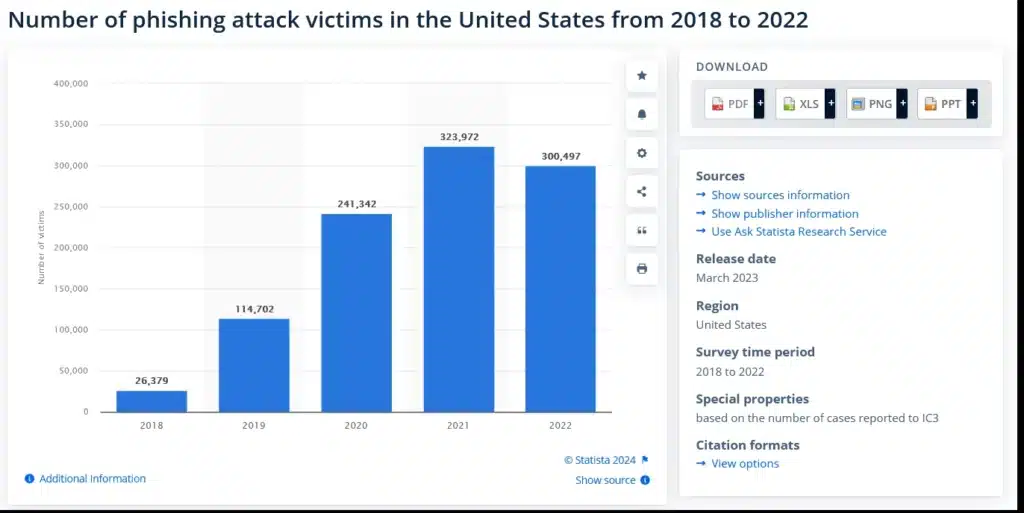
Source: Statista
Phishing attacks involve tricking you into divulging sensitive information like your usernames, passwords, credit card information, or other financial details. These attacks often come as deceptive emails, messages, or websites that impersonate trusted entities.
Social engineering is critical to phishing, exploiting human psychology to compromise security.
DDoS attacks
Distributed Denial of Service (DDoS) attacks entail flooding your network with traffic to overwhelm its resources and cause service disruptions. Cybercriminals often use botnets to orchestrate large-scale DDoS attacks. Mitigating these threats requires advanced network infrastructure and vigilant monitoring.
Secure communication channels, such as encryption, are crucial for thwarting these attacks.
SQL injection
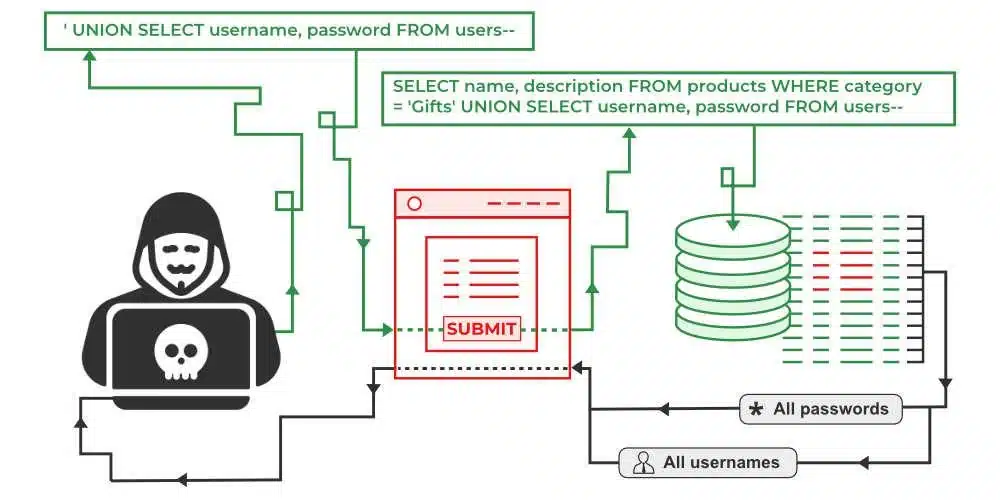
Source: geeksforgeeks
In SQL injection, attackers inject malicious SQL code into input fields, exploiting vulnerabilities in your website’s database. Successful SQL injections can result in unauthorized access, data manipulation, or even deletion.
Regular security audits and input validation are essential for preventing such attacks.
Zero-day exploits
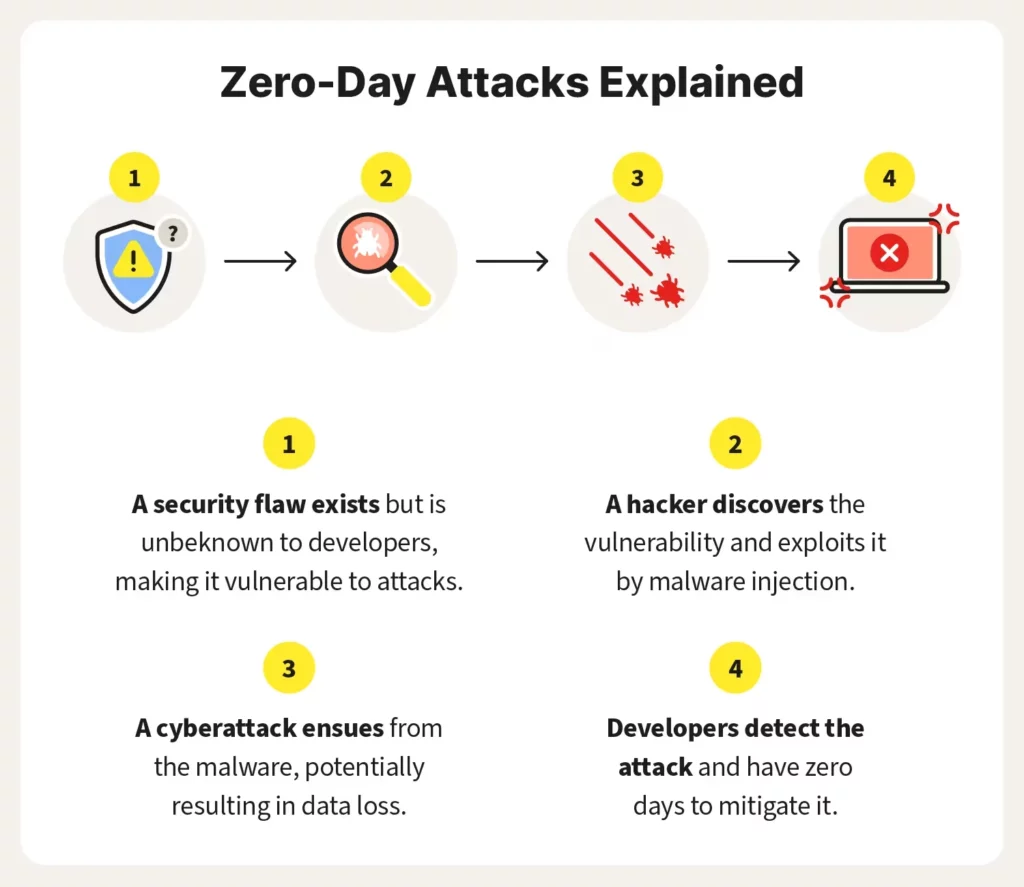
Source: Norton
Zero-day exploits target undisclosed vulnerabilities in software before developers can release patches or fixes. Cybercriminals capitalize on the window of opportunity between discovery and remediation.
Remaining vigilant, keeping your software up to date, and employing intrusion detection systems are vital in mitigating the risk of zero-day exploits.
Advanced Persistent Threats (APTs)
APTs involve sophisticated, prolonged attacks where cybercriminals gain unauthorized access to your system and remain undetected for an extended period. These threats are often state-sponsored and focus on stealing sensitive information or disrupting critical infrastructure.
Combating APTs requires a multi-layered defense strategy and constant threat intelligence monitoring.
IoT vulnerabilities
Insecure IoT devices can serve as attack vectors for hackers, leading to broader network compromises. Implementing robust security protocols for IoT devices and regular firmware updates are essential to mitigate these vulnerabilities.
Challenges in Cybersecurity
Several challenges hinder effective cybersecurity implementation as businesses and individuals navigate the digital landscape. As technology becomes more advanced, so do the tactics of cybercriminals and the complexity of the threats they pose to your data.
Understanding and dealing with these challenges is vital to maintaining the integrity and protection of your digital systems.
The human factor
Despite sophisticated technological defenses, the human element remains one of the most significant issues in cybersecurity. Social engineering attacks, like pretexting and phishing, exploit human psychology to manipulate you into disclosing sensitive information or performing actions that compromise security.
Education and awareness programs are essential to empower users and reduce the likelihood of falling victim to such tactics.
The evolving threat landscape
The threat landscape is dynamic and constantly evolves since cybercriminals continually develop new tactics, techniques, and procedures to bypass your security measures. Keeping up with the latest threats requires continuous monitoring, threat intelligence sharing, and proactive adaptation of cybersecurity strategies.
The sophistication of attacks
Advanced Persistent Threats (APTs) are highly sophisticated and targeted attacks typically conducted by well-funded and organized cyber criminals. APTs involve prolonged and stealthy operations aimed at exfiltrating your sensitive information or disrupting operations.
Detecting and mitigating APTs require advanced threat intelligence, sophisticated tools, and a comprehensive cybersecurity strategy.
Insider threats
Insiders with malicious intent or unintentional security lapses can pose a massive risk to your organization. Malicious insiders may exploit their privileged access to compromise your systems, steal sensitive data, or engage in sabotage.
Addressing insider threats involves monitoring user activities, implementing strict access controls, adopting a culture of security awareness, and employee training.
Supply chain vulnerabilities
The interconnected nature of supply chains introduces vulnerabilities that cybercriminals can exploit. Attacks on your suppliers, vendors, or partners can have cascading effects on interconnected systems.
Organizations must assess and manage the cybersecurity risks associated with their supply chain, ensuring that all entities involved adhere to robust security practices.
Resource constraints
Many organizations, especially small and medium-sized enterprises, face resource constraints regarding budget, skilled personnel, and technological infrastructure. Limited resources can hinder incorporating comprehensive cybersecurity measures, making these organizations attractive targets for cybercriminals.
Finding cost-effective solutions and leveraging cybersecurity best practices are critical for mitigating resource-related challenges.
Technological complexity
The increasing complexity of IT environments, with many devices, applications, and networks, poses challenges for cybersecurity management. Integrating and securing diverse technologies while ensuring your interoperability is a complex task.
Organizations must implement effective cybersecurity measures without sacrificing usability and efficiency.
Regulatory compliance
The regulatory landscape for cybersecurity has evolved, with numerous industry-specific regulations and compliance requirements. Your organization must navigate a complex web of rules, which often vary across regions, industries, and jurisdictions.
Achieving and maintaining compliance requires ongoing efforts and resources.
Incident response and recovery challenges
Despite your best efforts to prevent cyber incidents, you should prepare your organization to respond effectively when a security breach occurs. Challenges in incident response include timely detection, containment, communication, and recovery.
Effective Strategies for Safeguarding Businesses and Individuals
Despite the challenges, there are proactive strategies that businesses and individuals can adopt to enhance their cybersecurity posture. Effective strategies include cyber hygiene, risk assessment and management, endpoint security, data encryption and backup, and incident response planning.
Cyber hygiene: The foundation of security
Establishing a solid foundation of cyber hygiene is paramount and includes regular software updates, strong password policies, multi-factor authentication, and secure browsing habits. Training employees and others to recognize and report phishing attempts contributes to a resilient cybersecurity culture.
Risk assessment and management: Identifying vulnerabilities
Conducting regular risk assessments helps you and others identify potential vulnerabilities in their digital infrastructure. By understanding your specific threats, your organization can prioritize and allocate resources quickly and effectively to mitigate the most critical risks.
Risk management should be an ongoing process that prompts you to adapt to the evolving threat landscape.
Endpoint security: Protecting devices and networks
Endpoint security involves securing individual devices (such as computers, smartphones, and IoT devices) and any connected networks. Deploying robust antivirus software, firewalls, and intrusion detection systems safeguards your organization from malware and unauthorized access.
Virtual Private Networks (VPNs) are not just great for VPN streaming TV shows and movies—they also provide invaluable data protection for your organization and employees. Implement VPNs to secure communications, especially for remote workers accessing company resources.
Regularly monitoring and updating security protocols strengthen your defense against emerging threats.
Data encryption and backup: Mitigating ransomware risks
Encrypting sensitive data and implementing regular backup procedures are crucial defenses against ransomware attacks. Encryption protects data from unauthorized access, and regular backups ensure data can be restored without succumbing to extortion demands.
Cloud-based backup solutions provide a virtual safety net against physical data loss.
Incident response planning: Preparing for the inevitable
No system is entirely invulnerable, making incident response planning a critical component of cybersecurity. Establishing clear protocols for responding to security breaches, including communication plans, containment strategies, and collaboration with law enforcement, enables your organization to minimize the impact of a data breach and facilitate a swift recovery.
Collaboration and information sharing: Strengthening the collective defense
Cybersecurity requires collaboration among businesses, government agencies, and cybersecurity professionals. Sharing threat intelligence and your best practices enhances the collective defense against evolving cyber threats.
Industry-specific information-sharing platforms and forums play a crucial role in disseminating timely information.
Protect Yourselves And Your Businesses From Cyber Threats
Safeguarding individuals and businesses in the digital age demands a proactive and comprehensive approach to cybersecurity. The rapidly changing landscape of cyber threats requires constant vigilance to mitigate potential risks.
By understanding the evolving threat landscape, implementing effective cybersecurity measures, and adopting a culture of vigilance, businesses and individuals can navigate the digital world with confidence and resilience. The commitment to cybersecurity and a shared responsibility to ensure a secure and interconnected future becomes necessary as technology advances.
Author’s Bio

Ivan Serrano is a versatile and insightful writer specializing in business, technology, and finance since 2015. His compelling articles and analyses have graced the pages of publications like Bitcoin Magazine, SmallBizClub, StartupNation, Namecheap, and Time Doctor. With a knack for translating complex topics into engaging content, Ivan continues to be a sought-after voice in the intersection of modern technology and business trends.




