If you are a freelancer who works from home, a small office, or remotely from various locations, or if you own a digital agency that employs freelancers, you could be at risk for cyber security threats.
Hackers are everywhere and have numerous tools aimed at large and small businesses and the self-employed. From phishing to ransomware, even a freelancer can end up on a hacker’s radar, particularly if you have poor cybersecurity or none.
A concern for most freelancers is the cost of cybersecurity, especially when you are paid exclusively for core work and not for all the time spent researching or preparing.
This usually boils down to freelancers not investing time or money into specific cybersecurity. As a result, you are vulnerable to some degree.
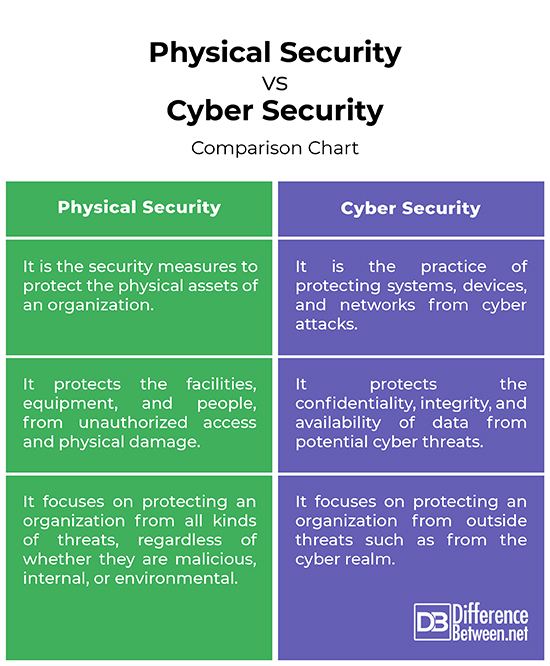
Physical vs. Cybersecurity: What’s the Difference?
When considering physical security vs. cyber security, these are two very different kinds of security operations.
Physical security refers to the physical assets you may have as a freelancer. This may be a home office, a studio, a business vehicle, or any type of physical equipment with which you accomplish your work.
Physical security will protect your property from theft, fire, vandalism, or environmental hazards such as inclement weather.
Cyber security refers to technology, methods, checks, and controls implemented to protect your online work, sensitive data storage, finances, and confidentiality as a freelancer.
This type of security has been designed to defend interconnected systems from identity theft, phishing, ransomware, malware, password compromise, and hacker attacks in general.
Thanks to advances in technology, they can be successfully integrated if need be to improve overall management even when doing so remotely.
Cybersecurity Concerns
As most freelancers now work online, cyber security is the priority.
When considering cybersecurity, the first step is to evaluate your security threat. Identifying what you need to protect and where your weaknesses lie will help you prioritize what to do and where to invest your money. Several potential hazards to consider include:
- How many devices do you use in your work? Smartphone, tablet, laptop, desktop, etc.? The more devices you use, the more ways a hacker can attack.
- Do you have an assistant or work in tandem with other professionals? If you do, additional devices and other users may be needed to consider when evaluating security risks.
- Do you use public Wi-Fi networks occasionally when traveling or working remotely? If you do, you must implement security measures to mitigate any risks when using public internet access.
- Are you using cloud-based applications or local applications? Many apps are integrated, meaning a weak link in one will be a weak one for all integrated apps.
- How do you store information, especially sensitive or personal data?
- Do you use NDAs when working with clients meaning that confidentiality is a priority?
- Do you store personal data that has legal ramifications, such as health, financial, student, or PIL-personally identifiable information?
- Is the internet necessary for you to be able to work? In the event of a cyberattack, work continuity is fundamental to be able to continue working.
Cybersecurity Tools for Freelancers
Whenever there is a security breach, some type of unauthorized access is connected to the violation.
Hence access control should be a priority when establishing cybersecurity protocols.
You need to have various tools at your disposal to protect against unauthorized access to your devices, work, and data.
Passwords
Password management is a crucial instrument in defending your online activities. Hackers generally use one of two methods to discover passwords:
- Password cracking attempts work when passwords are simplified, such as using the words “password,” “123456”, or similar. These passwords can generally be cracked within seconds.
- Social engineering permits hackers to discover sufficient information about you to make an educated guess, such as birthdates, middle names, or your dog’s name found on social media.
Using the same password on multiple sites only increases vulnerability. Using a password manager will generate a long password that the manager remembers, so you don’t have to.
Using a password manager is much safer than memorizing passwords on a browser.
Another advantage to a password manager is that it can store the login page for you.
In this way, you will not be apt to click on links that may be phishing scams. Your manager will offer added protection because it will not auto-fill a page where the URL is different.
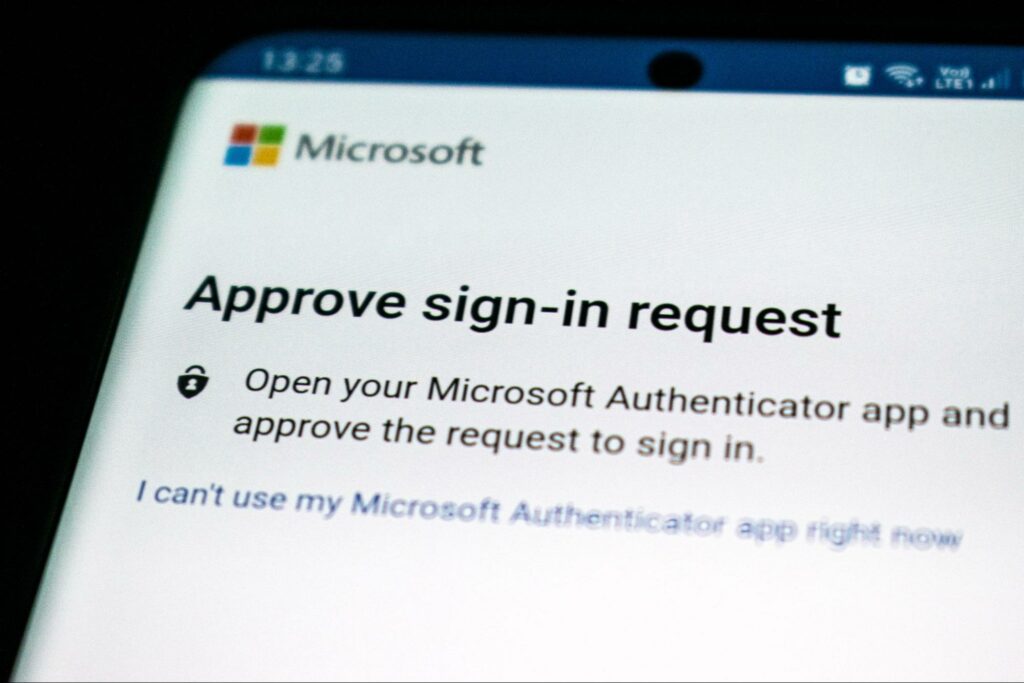
MFA – Multi-factor Authentication
Adding a layer of access control increases your protection tenfold. This prevents terrible players from accessing your apps even if they have discovered your password.
MFA may include using an authentication app, a one-time code that is delivered to you and expires after several minutes, or through delivery to another device like your smartphone.
Biometric authentication is increasingly popular, and new methods such as voice authentication.
Many apps already provide MFA in your device’s security settings. This double-layer protection is not only crucial for data storage but should be implemented for bank accounts, email, and any freelance software you may be using.
VPN – Virtual Private Network
If you travel a lot and depend on public internet connections, you should have a VPN at your disposal.
This software creates an encrypted connection for all your internet traffic so that hackers cannot intercept what you are transmitting.
Without a VPN, hackers can access unprotected communication that travels through public Wi-Fi whether in a public library, hotel lounge, airport café, or in the park. Even public internet using passwords is not entirely secure.
Even if your home or office internet connection should prove to be more secure than public Wi-Fi, it is worth the investment to use VPN when using the internet for work purposes. VPN should be installed on all devices you use, not just on your laptop or home computer.

Protection Software
Anti-virus, anti-malware, or firewall software is one step in the right direction, but it may not be sufficient. These protective measures do not include:
- Access restriction
- Cloud-based traffic threat detection
- Communication threat detection
- Patch scanning to verify if the software is updated
- Ransomware protection
As a freelancer, considering security suites for small businesses would be worth your while. Some of these security packages also protect you from hackers infiltrating your webcam or microphone, mainly if you use videoconferencing for work purposes.
Encryption for Data Storage
Even if your data storage is limited and perhaps does not have legally binding security requirements, it’s a good idea to avail yourself of the best security available when storing documents or sensitive data.
Encrypted storage, separate from cloud-based apps or the drive you use, will offer an extra layer of protection. Cloud-based encryption lockers or external encryption storage are essential options.
A complicated encryption key or password will be necessary regardless of what you use. Should you lose or forget this key, you will not be able to access the data you have stored. Office and Google also offer encryption options.
Secure Payments
Only accept secure payment methods such as PayPal, Payoneer, Skrill, or similar. Inform clients upfront what payment form is acceptable to you before you accept any work.

How to Be Prepared When Things Go Wrong
A significant threat with any security attack, whether physical or cyber, is the interruption of your business and livelihood.
For freelancers relying on a device and an internet connection, maintaining business continuity after any type of security mishap can be challenging and a question of survival.
Protection in the Case of Theft
If someone steals your laptop or you lose your smartphone, you could be in big trouble. Anti-theft software will limit the damage. It may include location tracking so you can find your device.
If the device was stolen, it might take photos of the perpetrator, and you may be able to reset a device completely, returning it to the factory settings. Some software may permit you to encrypt a device remotely.
Backups
Should you fall victim to hackers or ransomware, having all your work and data backed up somewhere else is worth it.
This way, you can deal with the attack while simultaneously working from another device. Backups can be cloud-based or done using external hardware, and it might be a good idea to use both.
But before you reinstall the backup, consider using antispy software to fix your phone in case it was hacked. Otherwise, you could compromise the data in your backup.
Consider having a backup device that is normally inactive without all your apps installed to protect it from the original hacking risk. Use an older machine that has been wiped clean but updated operating systems. In a pinch, you’ll be glad you have it.
The Bottom Line
Security is an ongoing daily challenge, and it is equally as important for freelancers who earn a living independently as it is for business owners with employees.
Start by identifying potential threats to your freelancing activities and researching solutions to meet those challenges. Continually reassess challenges and solutions.
As technology progresses, so will vulnerabilities. But if your business is strong, you’ll have the resources needed to meet those challenges.




